Pokemon Go is yet to be officially available in the Philippines therefore excited Android users are willing to side-load APKs downloaded outside Google’s Play Store. You might want to be careful though as a modified app infected with malware was spotted which has the capability to hijack your device.

The infected Pokemon Go Android app was spotted by Proofpoint – a security software company based in Sunnyvale, California. According to their findings, the infected app includes a “malicious remote access tool (RAT) called DroidJack (also known as SandroRAT), which would virtually give an attacker full control over a victim’s phone.”
Proofpoint said that the infected app was not observed in the wild but was uploaded to a a malicious file repository service on July 7, 2016 with a SHA256 hash of 15db22fd7d961f4d4bd96052024d353b3ff4bd135835d2644d94d74c925af3c4 (the legitimate app has a SHA256 hash of 8bf2b0865bef06906cd854492dece202482c04ce9c5e881e02d2b6235661ab67).
Users can also check the app’s permission settings to identify if it is infected. The image below shows the permissions settings of a legit app:
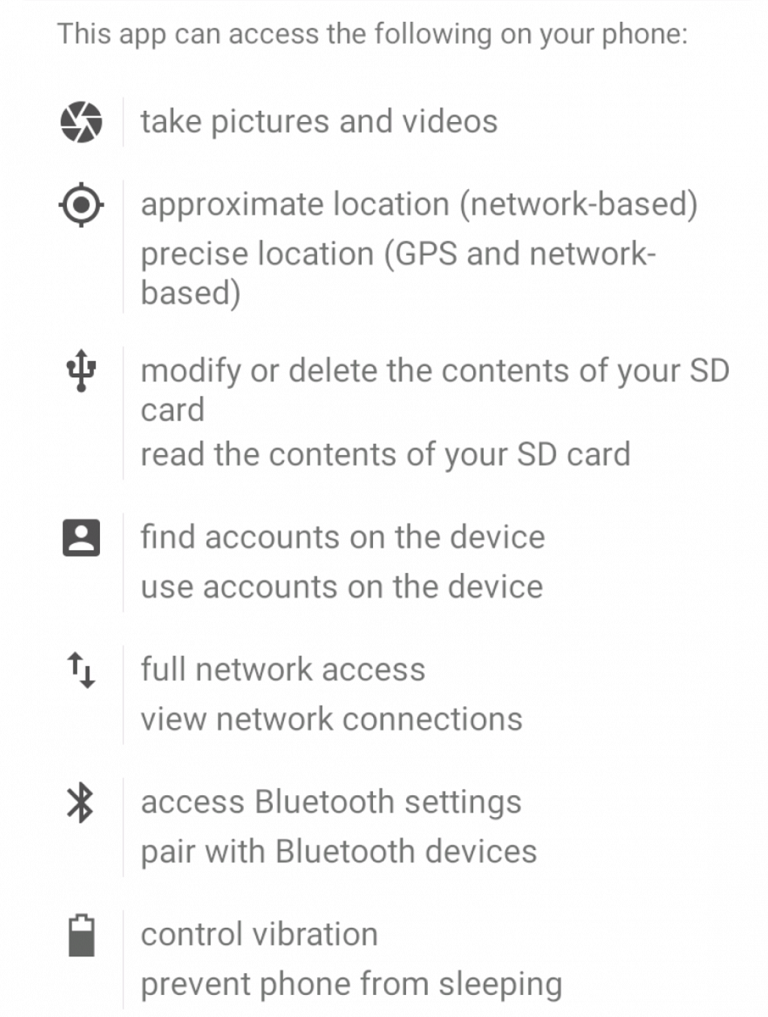
The permissions of an infected app has access to more settings including calls, SMS, audio recording, contacts, web bookmarks and history, and WiFi. See image below.

Users are advised to be careful when downloading and side-loading apps. To be sure, you can wait for the official release and download it straight from the Google Play Store when it becomes available.
source: Proofpoint
via: GSMArena

YugaTech.com is the largest and longest-running technology site in the Philippines. Originally established in October 2002, the site was transformed into a full-fledged technology platform in 2005.
How to transfer, withdraw money from PayPal to GCash
Prices of Starlink satellite in the Philippines
Install Google GBox to Huawei smartphones
Pag-IBIG MP2 online application
How to check PhilHealth contributions online
How to find your SIM card serial number
Globe, PLDT, Converge, Sky: Unli fiber internet plans compared
10 biggest games in the Google Play Store
LTO periodic medical exam for 10-year licenses
Netflix codes to unlock hidden TV shows, movies
Apple, Asus, Cherry Mobile, Huawei, LG, Nokia, Oppo, Samsung, Sony, Vivo, Xiaomi, Lenovo, Infinix Mobile, Pocophone, Honor, iPhone, OnePlus, Tecno, Realme, HTC, Gionee, Kata, IQ00, Redmi, Razer, CloudFone, Motorola, Panasonic, TCL, Wiko
Best Android smartphones between PHP 20,000 - 25,000
Smartphones under PHP 10,000 in the Philippines
Smartphones under PHP 12K Philippines
Best smartphones for kids under PHP 7,000
Smartphones under PHP 15,000 in the Philippines
Best Android smartphones between PHP 15,000 - 20,000
Smartphones under PHP 20,000 in the Philippines
Most affordable 5G phones in the Philippines under PHP 20K
5G smartphones in the Philippines under PHP 16K
Smartphone pricelist Philippines 2024
Smartphone pricelist Philippines 2023
Smartphone pricelist Philippines 2022
Smartphone pricelist Philippines 2021
Smartphone pricelist Philippines 2020
Rence says:
hahaha, andaming permission na dapat d kasama ah